Next generation antivirus (NGAV) differs from the traditional antivirus solutions we’ve been using for years by incorporating many additional controls, functions and features. NGAV has the ability to learn behavior at the endpoints. They identify anomalous behavior without any download or matching to virus signature database. Advance to an Autonomous Breach Protection solution with managed detection and response (MDR) that covers your users, host’s, Files and Network. Go beyond just the next generation to the extended generation for the future of protecting your endpoints.
Traditional antivirus has lost its effectiveness as operating systems, software, computer networks and digital threats have become more sophisticated. The rapid growth in the number of threats is continuous and includes new malware and creative variations, which makes traditional signature-based approaches ineffective. Seemingly benign events in one part of the network may be an indicator of a bigger attack when correlated across any one of four pillars of the computing environment – users, network, files or the endpoint device.
Pandemic 2020 has made us rethink many things about how our companies do business. It has instilled the need for a closer look at the kinds of attacks occurring across the world. Home users with unpatched and poorly maintained systems may be accessing our networks and even through a multi-factor authenticated VPN that can still be a problem. Modern attacks possess a considerable threat to organizations that do not have advanced protection in place:
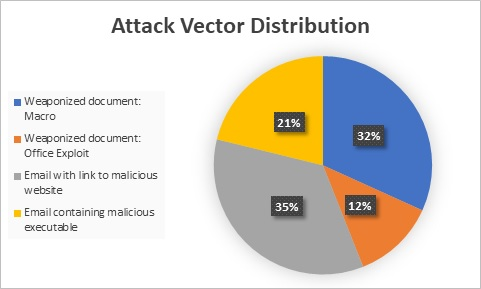
While 21% of emails featured simplistic attacks; a link to a malicious executable, memory attacks, most undesirable links include advanced capabilities such as malicious Macros and exploits or redirection to malicious websites – a challenge met easily with an Autonomous Breach Protection solution. Especially one with extended capabilities that is managed 24x7x365 days a year. One that doesn’t sleep when you do and is awake when the attackers are.
When taking a closer look at how modern attacks would be blocked by a tool that has the extended detection and response (XDR) enhanced controls verifies that the more creative attacks must be regarded as a serious risk potential:
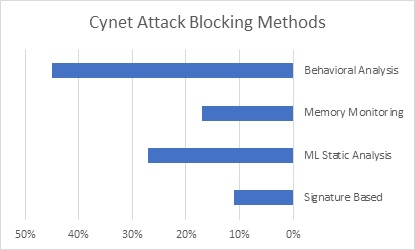
This graphic of Attack Blocking Methods illustrates that only around 10% would be blocked by traditional antivirus solutions. That means using the old signature-based architecture.
XDR (Extended Detection and Response): Autonomous Breach Protection
Gartner defines XDR as a “unified security incident detection and response platform that automatically collects and correlates data from multiple security components.” Operationally, XDR takes a holistic approach to cybersecurity, leveraging big data, ML and analytics to deliver on the promise of integrating best-in-breed components. Proprietary XDR implementations limit themselves to one vendor’s product portfolio; open ones combine the best of the cybersecurity ecosystem and avoid vendor lock-in.
Gartner’s 2017 Market Guide for Endpoint Detection and Response Solutions considers endpoint detection and response (EDR) as a basic security capability, part of what should be considered the foundation of any solution. The Cynet XDR platform monitors and leverages the combined signals from Endpoint Users, Network, Files and hosts; then includes Deception Technology or what you may have heard called Honeypots – which could otherwise be an additional expense and maybe another vendor to manage. By adding managed services (MDR), SIEM-like capabilities and correlating across these four pillars; solutions have extended to the attack points that can more fully protect your computing environment. Extended Autonomous Breach Protection more accurately identifies suspicious and unauthorized activities, preventing the behaviors outright and enabling proactive response and remediation to advanced malicious threats than ever before. Using pre-defined or your-defined Playbooks ransomware, zero day and many yet unknown attacks can be stopped in their tracks.
To help NGAV solutions identify threats that slip past traditional AV, XDR provides a holistic approach to data collection, which in turn powers machine learning, predictive analytics, and behavior monitoring, showing a complete picture of the environment. Providing complete transparency into the endpoint and even vulnerability detection reporting. Together, these technologies help companies monitor events and identify patterns that may be suspicious, turning them into attack visualizations that power Autonomous Breach Protection.
XDR can help discover even the most minute changes in files, registries, and networks. Being able to do that helps uncover malicious activity hidden in plain sight. Being able to do that provides the forensics data that you’ll need to find the root cause of a potential problem in your network. With that insight XDR helps responders contain the identified threats and block emerging, never-seen-before attacks that will often otherwise slip through most NGAV solutions or even those solutions that don’t extend to address all four pillars (user, file, network, device).
So what exactly are some differences that you gain with NGAV?
- No signatures
- No weekly updates
- No recurring scans
- No performance overhead
NGAV solutions that are most effective will use innovative technologies to prevent the rapidly changing tactics, techniques, and procedures (TTPs) used by the bad guys today to breach organizations, including traditional malware, zero-day attacks and even advanced malware-free or file-less attacks. They will have access to world class indicators of compromise and use them to prevent an attack in your network before it can do any damage.
Replace Outdated Antivirus
Organizations gain an unprecedented level of visibility into attempted attacks with ability to easily search for the forensics of the attack and have a fully managed detection and response team backing them. This provides the details and context necessary to offer Extended Autonomous Breach Protection, see what’s happening on the endpoint and know how to remediate. How many other lessor quality solutions could you replace if you had an Extended Detection and Response (XDR) solution and the support of a world class CyOps team backing you up 24x7x365.
Is now a good time to replace your traditional AV? Call or email FIPCO’s Rob Foxx at 800-722-3498 ext. 249 or itservices@fipco.com today to take advantage of these services and ensure the safety and soundness of your business.